Check for unpatched CVEs on Mac with Jamf Pro using SOFA
Introduction

My initial post about SOFA gave two simple examples of Extension Attribute scripts that can be used to target actions in Jamf Pro, one based on whether a computer is up to date, and another based on whether XProtect is up to date.
SOFA also exposes lists of CVEs that are reported as patched. It also identifies CVEs that Apple have reported as being actively exploited - so called “zero day” vulnerabilities. Graham Gilbert has already published a blog post about how to leverage this data using OSQuery in his post Investigating unpatched CVEs with osquery and SOFA. Here, I describe how to use an extension attribute script in Jamf Pro to show if there are any unpatched CVEs and if any of those are zero-day exploits.
Rationale
For most organisations, verifying that the Mac is patched may be sufficient for determining compliance and conditional access to an organisation’s resources. But given the ongoing difficulties of patching macOS in real world scenarios, some organisations may choose only to enforce compliance against known CVEs or, indeed, only against known zero-day exploits.
CVE Check Extension Attribute
The Extension Attribute script I provided in the SOFA GitHub is named macOSCVECheck-EA.sh (click here). This checks if the local system is running the current minor version of macOS, and, if not, counts the number of CVEs and zero-day CVEs reported in all newer versions of macOS in the SOFA JSON feed. This is reported to Jamf Pro in the following form, where the total reported CVEs are shown first, followed by the number of zero-day exploits:
CVEs:25, ActiveExploits:2
This can then be used to scope non-compliant computers into a Smart Group, which can be used to push MDM/DDM software update commands or any other compliance- or conditional access-related action.
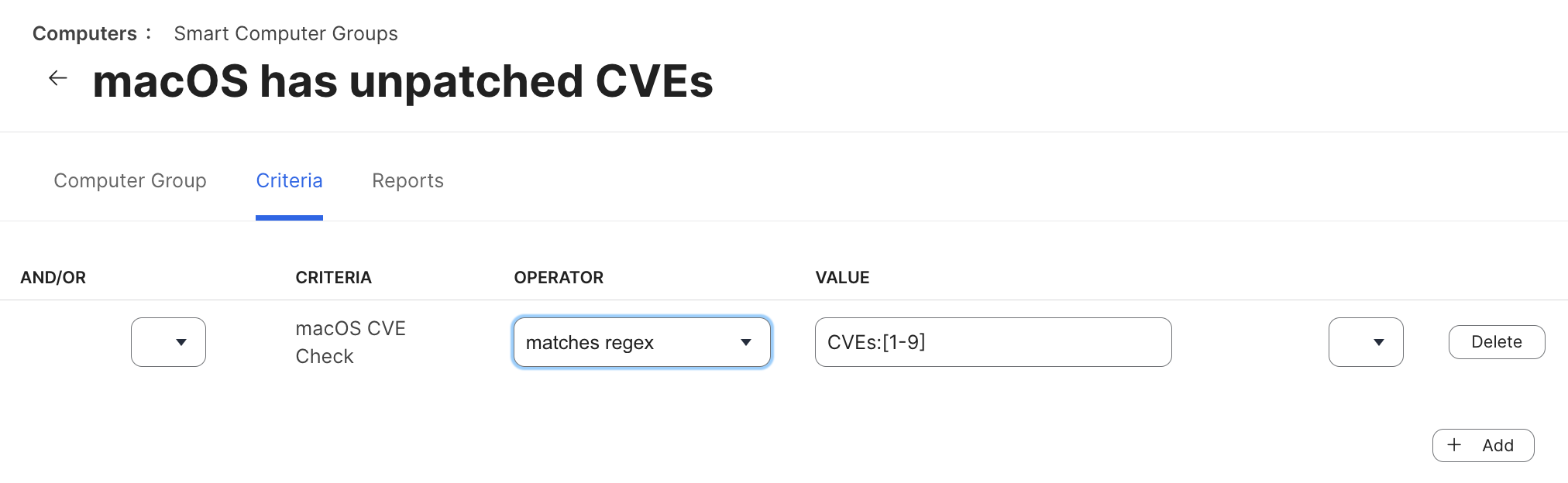
In the first example, we have named the Extension Attribute macOS CVE Check. The Smart Group is named macOS has unpatched CVEs. The single criterion is that macOS CVE Check matches regex CVEs:[1-9]. This regex includes any number of CVEs greater than 0.
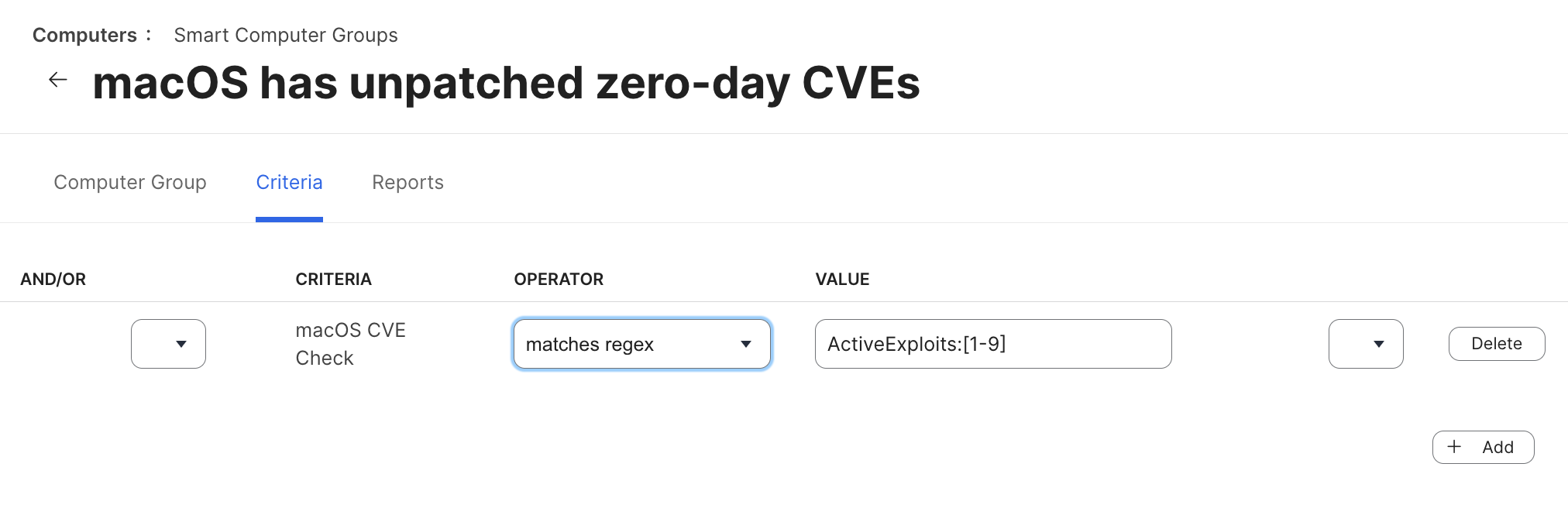
In the second example, the Smart Group is named macOS has unpatched zero-day CVEs. The single criterion is that macOS CVE Check matches regex ActiveExploits:[1-9]. This regex includes any number of zero-day CVEs greater than 0.
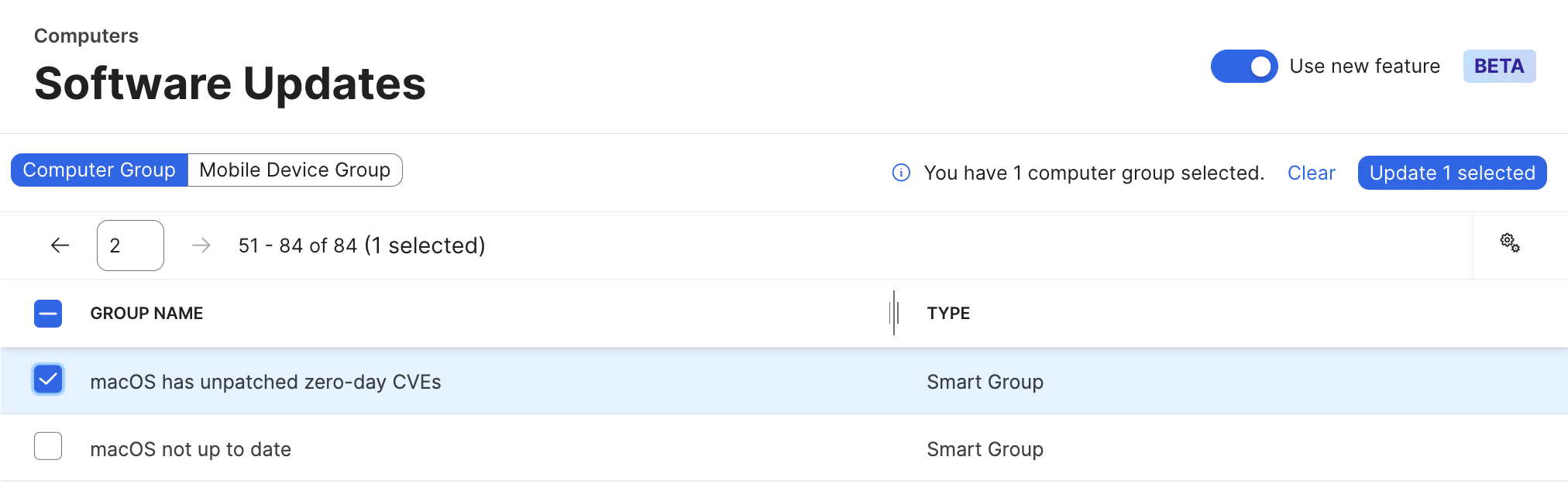
Here, we use this smart group in Software Update to initiate MDM update commands.
Conclusion
Here is one more example of how Jamf Pro Admins can utilise data provided from SOFA to trigger security-related processes in Jamf Pro.
If you want to keep up to date on the SOFA project and associated resources, check out the #macadmins-opensource channel in the Mac Admins Slack Workspace.